CKEditor 5 is Now SOC 2 Type 2 Compliant
We know that security is an important factor when choosing components for your applications. As part of CKEditor’s commitment to meeting our user’s growing needs in this area, we’ve been focusing on ensuring that we offer a robust and secure solution.
Today, we’re excited to announce our most recent accomplishment in cementing users’ confidence in our editor’s security. CKEditor is pleased to announce we’ve achieved SOC 2 Type 2 compliance certification! This achievement goes hand in hand with last year’s announcement of reaching SOC 2 Type 1 compliance.
These certifications confirm that our security, availability, and confidentiality controls are not only well-designed but are also consistently maintained and effective over time. This milestone reinforces our dedication to providing secure, reliable solutions that our customers can trust.
What is SOC 2 Type 2 Compliance?
SOC 2 Compliance certification, issued by the American Institute of Certified Public Accountants (AICPA), assesses how effectively a company manages customer data according to industry best practices.
Key Aspects of SOC 2 Type 2 Compliance
Security
CKEditor has implemented and continuously maintains rigorous security measures to protect data from unauthorized access. This includes encryption, authentication, and strict access controls. Regular security audits, continuous monitoring, and proactive threat detection are integral to identifying and mitigating potential risks. SOC 2 Type 2 compliance confirms that these controls are not only designed properly but also operate effectively over an extended period.
Availability
Our infrastructure is designed for high availability. SOC 2 Type 2 compliance verifies that CKEditor’s systems are consistently reliable and accessible. Redundant systems, failover mechanisms, and comprehensive disaster recovery strategies ensure minimal downtime and uninterrupted service for our users.
Confidentiality
We enforce strict controls to safeguard confidential information. This includes access restrictions, data classification protocols, and encryption practices. SOC 2 Type 2 compliance certifies that these controls are continuously followed and monitored to prevent unauthorized disclosure of sensitive data.
Trust and Transparency
Achieving SOC 2 Type 2 compliance highlights our long-term commitment to protecting customer data. This certification is a testament to our dedication to transparency, proving that CKEditor’s security practices are regularly tested and verified by independent auditors.
Audit Scope
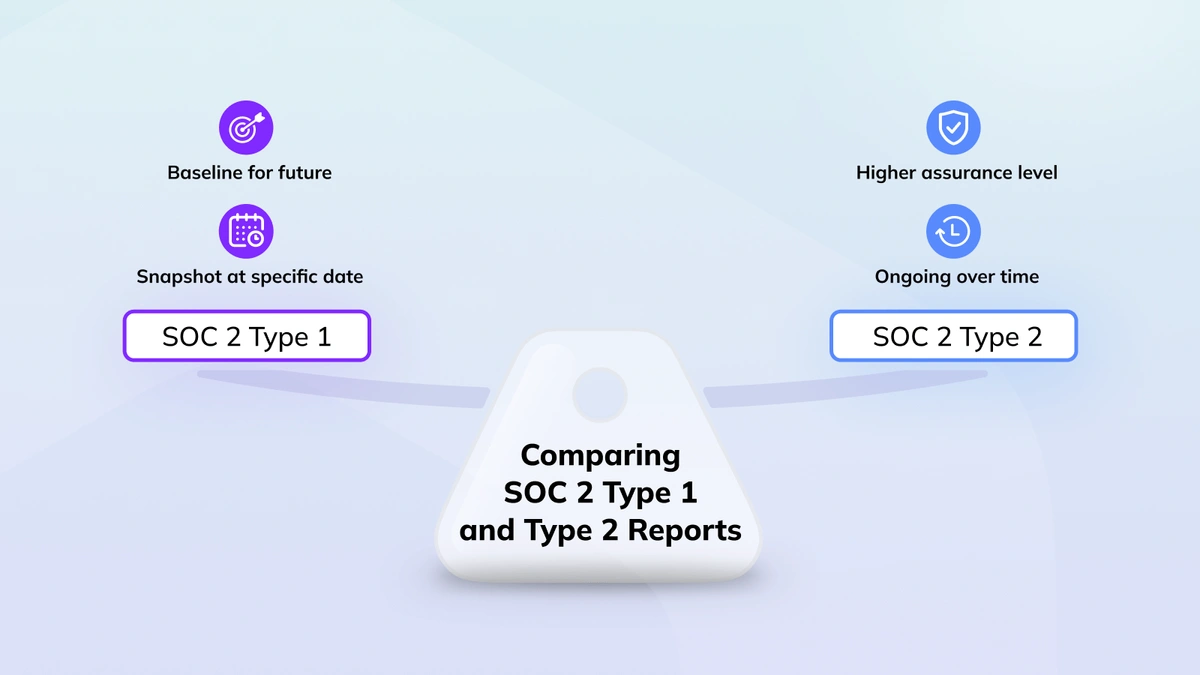
Unlike SOC 2 Type 1, which evaluates the design of security controls at a single point in time, SOC 2 Type 2 assesses how effectively these controls operate over a defined audit period. This means that CKEditor’s security, availability, and confidentiality measures have been rigorously evaluated over months of operation, confirming they perform as intended.
GDPR Compliance
CKEditor 5 remains fully compliant with the General Data Protection Regulation (GDPR). Whether you choose our cloud or self-hosted solutions, CKEditor supports your organization’s goals in meeting stringent data privacy requirements. we’re committed to protecting your users’ personal data at every stage of content creation and management.
Cloud Security
Security is at the core of CKEditor’s cloud-based products, including Real-Time Collaboration (RTC), Document Converters, and self-service cloud solutions.
Cloud Security Features:
-
End-to-End Encryption: Data is encrypted both in transit and at rest, establishing data security throughout its lifecycle.
-
Access Controls: Strict authentication and authorization policies verify that only approved users can access sensitive data.
-
Continuous Monitoring: Automated monitoring systems and regular security audits help detect and respond to potential threats in real-time.
-
Resilient Infrastructure: Our cloud environment includes built-in redundancy and disaster recovery measures to maintain service availability.
Real-Time Collaboration
Built with secure WebSockets, our Real-Time Collaboration tools make sure that data shared during collaborative sessions is always protected.
Document Converters
Our document processing engines operate in secure environments with data encrypted throughout the conversion process.
Self-Hosted Security
For customers who prefer on-premises deployment, CKEditor Cloud Services On-Premise offers complete control over your security configurations. Our self-hosted solutions are designed for flexibility, allowing organizations to tailor security measures to their specific infrastructure needs.
Security Features for Self-Hosted Solutions:
-
Content Security Policy (CSP): Protect your application against cross-site scripting (XSS) attacks by restricting resource loading and execution.
-
Granular Permissions: Assign fine-tuned permissions with read-only or comments-only modes for different user groups.
-
Role-Based Access Control (RBAC): Secure sensitive content by assigning access rights based on user roles.
Content Security Policy (CSP)
CKEditor fully supports Content Security Policy (CSP) to mitigate security risks like XSS attacks. By limiting the sources from which resources can be loaded, CSP adds an extra layer of security to your applications. Implementing CSP with CKEditor is simple and effective in strengthening your security posture.
Conclusion
Achieving SOC 2 Type 2 compliance marks a significant milestone in CKEditor’s ongoing commitment to providing secure and reliable solutions. This certification confirms that our security controls are not only well-designed but also consistently effective over time. Whether you use CKEditor in the cloud or self-hosted, you can trust that your data is secure.
For more information, explore our detailed security documentation. If you have specific questions about how CKEditor can meet your security needs, please contact us.